0x00 Preface
This article will combine your own experience, refer to a variety of open source tools and materials, try to summarize this skill, share learning experience
Reference to open source tools and materials:
- Hot Potato: https://github.com/foxglovesec/Potato
- Tokenvator: https://github.com/0xbadjuju/Tokenvator/
- Powershell version Hot Potato: https://github.com/Kevin-Robertson/Tater
- Rotten Potato: https://github.com/breenmachine/RottenPotatoNG
- lonelypotato: https://github.com/decoder-it/lonelypotato
- Juicy Potato: https://github.com/ohpe/juicy-potato
- https://github.com/hatRiot/token-priv
- https://foxglovesecurity.com/2017/08/25/abusing-token-privileges-for-windows-local-privilege-escalation/
- https://foxglovesecurity.com/2016/01/16/hot-potato/
- https://foxglovesecurity.com/2016/09/26/rotten-potato-privilege-escalation-from-service-accounts-to-system/
- https://foxglovesecurity.com/2017/08/25/abusing-token-privileges-for-windows-local-privilege-escalation/
0x01 Introduction
This article will introduce the following:
- Brief use of ideas
- SeImpersonatePrivilege permissions corresponding to the use of ideas and open source code
- SeAssignPrimaryPrivilege permission corresponding to the use of ideas and open source code
- SeTcbPrivilege permissions corresponding to the use of ideas and open source code
- SeBackupPrivilege permissions corresponding to the use of ideas and open source code
- SeRestorePrivilege permissions corresponding to the use of ideas and open source code
- SeCreateTokenPrivilege permissions corresponding to the use of ideas and open source code
- SeLoadDriverPrivilege permissions corresponding to the use of ideas and open source code
- SeTakeOwnershipPrivilege permissions corresponding to the use of ideas and open source code
- SeDebugPrivilege permissions corresponding to the use of ideas and open source code
0x02 Brief use of ideas
1. After obtaining the access rights of the target, view the available permissions.
whoami /priv
For example, the normal user has the following permissions
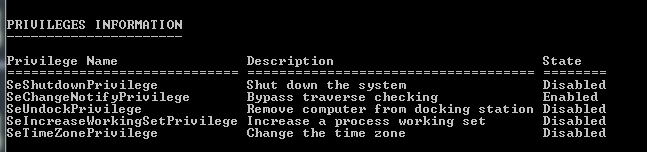
The admin user has the following permissions
The permissions of the iis user are as follows
The Privilege Name item indicates the privilege, and the State indicates the privilege status. We can set the privilege to Disabled or Enabled via WinAPI AdjustTokenPrivileges.
Implementation code for reference:
https://github.com/3gstudent/Homework-of-C-Language/blob/master/EnablePrivilegeandGetTokenInformation.cpp
The code implements the specified permission (SeDebugPrivilege) and looks at the current user name and permissions
2, if you include the following nine permissions, we can further use it
- SeImpersonatePrivilege
- SeAssignPrimaryPrivilege
- SeTcbPrivilege
- SeBackupPrivilege
- SeRestorePrivilege
- SeCreateTokenPrivilege
- SeLoadDriverPrivilege
- SeTakeOwnershipPrivilege
- SeDebugPrivilege
Note:
Users of iis or sqlserver usually have SeImpersonatePrivilege and SeAssignPrimaryPrivilege permissions
Backup service users usually have SeBackupPrivilege and SeRestorePrivilege permissions
0x03 SeImpersonatePrivilege permission utilization
Reference materials:
https://github.com/hatRiot/token-priv/blob/master/abusing_token_eop_1.0.txt#L327
SeImpersonatePrivilege
Impersonatea client after authentication
A process with this privilege can impersonate an existing token but cannot create a new token
The following users have this privilege:
- Local Administrators group member and local service account
- Service initiated by the Service Control Manager
- A COM server that is started by the Component Object Model (COM) infrastructure and configured to run under a specific account
Usually, iis or sqlserver users have this privilege
Use ideas
- Use the NTLM Relay to Local Negotiation to get the System user's Token. Use the open source tool Rotten Potato, lonelypotato or Juicy Potato.
- Create a new process with WinAPI CreateProcessWithToken. The Token of the System user has the SeImpersonatePrivilege permission to create successfully.
- The token has System privileges
Test code for reference:
https://github.com/3gstudent/Homework-of-C-Language/blob/master/EnableSeImpersonatePrivilege.cpp
The code implements the SeImpersonatePrivilege permission to open the current process, calls CreateProcessWithToken, passes in the current process's Token, creates a process, and cooperates with RottenPotato, which can be used to lift the right from LocalService to System permission.
0x04 SeAssignPrimaryPrivilege permission utilization
Reference materials:
https://github.com/hatRiot/token-priv/blob/master/abusing_token_eop_1.0.txt#L359
SeAssignPrimaryPrivilege
Assign tokens to processes (newly created or suspended processes)
Usually, iis or sqlserver users have this privilege
Use idea 1
- Get the Token of the System User with NTLM Relay to Local Negotiation
- Create a new process through WinAPI CreateProcessAsUser, and pass in the Token of the System user.
- The token has System privileges
Test code for reference:
https://github.com/3gstudent/Homework-of-C-Language/blob/master/EnableSeAssignPrimaryTokenPrivilege.cpp
The code implements the SeAssignPrimaryTokenPrivilege permission to open the current process, calls CreateProcessAsUser, passes the Token of the current process, creates a process, and cooperates with RottenPotato, which can be used to grant rights from LocalService to System permission.
Use ideas 2
- Get the Token of the System User with NTLM Relay to Local Negotiation
- Create a new pending process via WinAPI CreateProcess with the parameter set to CREATE_SUSPENDED
- Replace the token of the new process with the Token of the System user via WinAPI NtSetInformationProcess
- The token has System privileges
0x05 SeTcbPrivilege permission utilization ideas
Reference materials:
https://github.com/hatRiot/token-priv/blob/master/abusing_token_eop_1.0.txt#L418
SeTcbPrivilege
Equivalent to the highest authority of the system
Use ideas
- Call LsaLogonUser to get the Token
- Add the Token to the Local System account group
- The token has System privileges
Test code for reference:
https://github.com/3gstudent/Homework-of-C-Language/blob/master/EnableSeTcbPrivilege.cpp
The code implements the SeTcbPrivilege permission to open the current process, log in to user test1, add it to the Local System account group, obtain System permissions, and create a registry key.
HKEY_LOCAL_MACHINE\SOFTWARE\testtcb0x06 SeBackupPrivilege permission utilization ideas
Reference materials:
https://github.com/hatRiot/token-priv/blob/master/abusing_token_eop_1.0.txt#L495
SeBackupPrivilege
Used to implement backup operations and have read access to any file in the current system.
Use ideas
- Read the registry
HKEY_LOCAL_MACHINE\SAM,HKEY_LOCAL_MACHINE\SECURITYandHKEY_LOCAL_MACHINE\SYSTEM - The commands for exporting all user hash mimikatz of the current system are as follows:
lsadump::sam /sam:SamBkup.hiv /system:SystemBkup.hiv
Test code for reference:
https://github.com/3gstudent/Homework-of-C-Language/blob/master/EnableSeBackupPrivilege.cpp
The code implements the SeBackupPrivilege permission to open the current process, reads the registry, saves it as a file
C:\\test\\SAM, C:\\test\\SECURITYandC:\\test\\SYSTEM0x07 SeRestorePrivilege permission utilization ideas
Reference materials:
https://github.com/hatRiot/token-priv/blob/master/abusing_token_eop_1.0.txt#L528
SeRestorePrivilege
Used to implement recovery operations, have write access to any file in the current system
Use idea 1
- Get SeRestorePrivilege permission, modify the registry
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options - Hijacking the start of the exe file
- Realize the privilege or as a back door
Use ideas 2
- Get SeRestorePrivilege permission, write dll file to any path
- Implement dll hijacking
- Realize the privilege or as a back door
Test code for reference:
https://github.com/3gstudent/Homework-of-C-Language/blob/master/EnableSeRestorePrivilege.cpp
The code implements the SeRestorePrivilege permission to open the current process, creating a registry key
HKEY_LOCAL_MACHINE\SOFTWARE\testrestore0x08 SeCreateTokenPrivilege permission utilization
Reference materials:
https://github.com/hatRiot/token-priv/blob/master/abusing_token_eop_1.0.txt#L577
SeCreateTokenPrivilege
Used to create a Primary Token
Use ideas
- Create a Primary Token via WinAPI ZwCreateToken
- Add Token to the local administrator group
- The token has System privileges
Test code for reference:
https://github.com/3gstudent/Homework-of-C-Language/blob/master/EnableSeCreateTokenPrivilege.cpp
The code implements the SeCreateTokenPrivilege permission to open the current process, creates a Primary Token, adds it to the local administrator group, and enables the SeDebugPrivilege and SeTcbPrivilege permissions.
0x09 SeLoadDriverPrivilege permission utilization ideas
Reference materials:
https://github.com/hatRiot/token-priv/blob/master/abusing_token_eop_1.0.txt#L626
SeLoadDriverPrivilege
Used to load the driver file
Use ideas
- Create a registry of driver files
reg add hkcu\System\CurrentControlSet\CAPCOM /v ImagePath /t REG_SZ /d "\??\C:\test\Capcom.sys"
reg add hkcu\System\CurrentControlSet\CAPCOM /v Type /t REG_DWORD /d 1
- Load driver file Capcom.sys
- Capcom.sys has a vulnerability. After the system is loaded, it can be upgraded from normal user rights to System permissions. The code can be referenced: https://github.com/tandasat/ExploitCapcom
- Get System privileges
Test code for reference: https://github.com/3gstudent/Homework-of-C-Language/blob/master/EnableSeLoadDriverPrivilege.cpp
The code implements the SeLoadDriverPrivilege permission to open the current process, reads the registry key
hkcu\System\CurrentControlSet\CAPCOM, and loads the driver file.Capcom.sys0x0A SeTakeOwnershipPrivilege permission utilization ideas
Reference materials:
https://github.com/hatRiot/token-priv/blob/master/abusing_token_eop_1.0.txt#L688
SeTakeOwnershipPrivilege
Similar to SeRestorePrivilege, it has write permission to any file in the current system.
Use idea 1
- Get SeTakeOwnershipPrivilege permission, modify the registry
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options - Hijacking the start of the exe file
- Realize the privilege or as a back door
Use ideas 2
- Get SeTakeOwnershipPrivilege permission, write dll file to any path
- Implement dll hijacking
- Realize the privilege or as a back door
Test code for reference:
https://github.com/3gstudent/Homework-of-C-Language/blob/master/EnableSeTakeOwnershipPrivilege.cpp
The code implements the SeTakeOwnershipPrivilege permission to open the current process, modify
hklm\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Optionsthe permissions of the registry key , and the normal user rights have full operation rights.
Subsequent write operations:
reg add "hklm\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options" /v takeownership /t REG_SZ /d "C:\\Windows\\System32\\calc.exe"
0x0B SeDebugPrivilege permission utilization ideas
Reference materials:
https://github.com/hatRiot/token-priv/blob/master/abusing_token_eop_1.0.txt#L736
SeDebugPrivilege
Used to debug specified processes, including reading and writing memory, often used to implement dll injection
Use ideas
- Find the process of System permissions
- Dll injection
- Get System privileges
Test code for reference:
https://github.com/3gstudent/Homework-of-C-Language/blob/master/EnableSeDebugPrivilege.cpp
The code implements the SeDebugPrivilege permission to open the current process, injecting dll into the specified process.



No comments:
Post a Comment