I found one interesting post in medium which is here and i got some idea to bypass UAC .
And I notice windows store (wsrest.exe) which is enable access by user.
and I copied it to Desktop and I check it at the process monitor . I found some missing dll in that .
Then, I start try to inject and Compile with above technique . And I'm also wrote the exploit code in C .
g0ttcha !!!
exploit code that I wrote : https://github.com/sailay1996/UAC_bypass_windows_store
Thanks for reading .




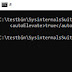


it says "spawnning shell as administrator". What do i do?
ReplyDeleteThis comment has been removed by the author.
ReplyDeleteIf your looking for Online Illinois license plate sticker renewals then you have need to come to the right place.We offer the fastest Illinois license plate sticker renewals in the state. UK RDP
ReplyDeleteDaily updated Telugu Sex Stories and Telugu kama kathalu
ReplyDeletetelugu sex kathalu
telugu sex
telugu stories
telugu kathalu
telugu boothu kathalu
telugukamakathalu
Audiotelugusexstories
Anuntytelugusexstories
Telugusexstories
kamakathalu-
hi was just seeing if you minded a comment. i like your website and the thme you picked is super. I will be back.
ReplyDeletebuy windows 10 pro product key
This is a wonderful article, Given so much info in it, These type of articles keeps the users interest in the website, and keep on sharing more ... good luck Ramen deuren
ReplyDeleteIt was wondering if I could use this write-up on my other website, I will link it back to your website though.Great Thanks. Ramen en deuren Leuven
ReplyDeleteWe have sell some products of different custom boxes.it is very useful and very low price please visits this site thanks and please share this post with your friends. 성인용품점
ReplyDeleteI was looking at some of your posts on this website and I conceive this web site is really instructive! Keep putting up.. カナダ観光ビザ
ReplyDeleteThis article gives the light in which we can observe the reality. This is very nice one and gives indepth information. Thanks for this nice article. Neuseeland Visum beantragen
ReplyDelete