Product version : 10.5.63.37653
Operating System tested on: Windows 10 1909 (x64)
Vulnerability: Origin Client Service DACL Overwrite Elevation of Privilege
Description :
When origin client application is installed, it created 2 different services which are "origin client service" and "origin web helper service" with different privilege that're "NT AUTHORITY\SYSTEM" and "NT AUTHORITY\Local Service". And also that services could be run by everyone.
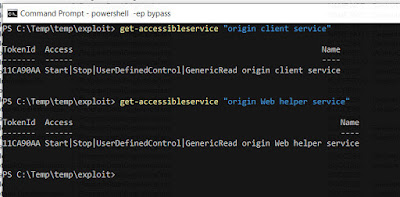 |
| Services Access Control |
 |
| create local.xml |
| SetSecurityFile(DACL) |
So, low privileged users can use this services to set permission (DACL) on High privileged files by creating symbolic link. Then, I used symboliclink-testing-tools which have been created by James Forshaw (@tiraniddo) from Project Zero to create symbolic link.
I created Hardlink on "C:\ProgramData\Origin\local.xml" to point the file "C:\windows\win.ini" which doesn't have access control by low privileged users. Then, I restart the service.
 |
| Set permission(DACL) on privileged file. |
To get SYSTEM shell with this bug, we can use "from-arbitrary-file-overwrite-to-system" of @decoder_it . I modified it as simple.
FileWrite Weapon: https://github.com/sailay1996/FileWrite2system
To Exploit this bug,
Create hardlink to file "C:\Windows\System32\DriverStore\FileRepository\prnms003.inf_amd64_e4ff50d4d5f8b2aa\Amd64\PrintConfig.dll", then you can get fully control access on that dll file PrintConfig.dll . After you get fully control , run that powershell script and you will get SYSTEM shell .
 |
| nt authority\system |
B00m !!!! You g0t SYSTEM shell.
And, I created the fully poc code for this bug.
https://github.com/sailay1996/origin_client_LPE
 |
| SYSTEM |
pwnedddd !!!! xD
Thanks for reading
@404death



No comments:
Post a Comment