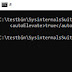
The LOCAL file type is primarily associated with DLL Redirection by Microsoft Corporation. 'DLL Hell' is a term, know too well for comfort between Microsoft Windows developers. 'DLL Hell' causes grief and despair when two (2) separate and essentially incompatible versions of a DLL file with the same name are installed with one over-writing the other. This can cause the first program whose DLL got over-written to stop functioning. Enter .local that redirects windows where to search for a specific dll. If a file application.exe.local exists, Windows will first look in that application's directory for the DLL file. If .local is a directory / folder, Windows will search in that directory instead of the application directory.
Ref: https://docs.microsoft.com/en-us/windows/win32/dlls/dynamic-link-library-redirection
comming soon: what can we do with that *.local for windows exploitation?
Thursday, May 21, 2020
What is NTDLL.DLL ?
Short Description :
A system-wide DLL, implementing the Windows native API. This is the lowest layer of code which is still in user mode. Its most important role is to make the transition to kernel mode for system call invocation. NTDLL also implements the Heap Manager, the Image Loader and some part of the user-mode thread pool. Although the native API is mostly undocumented.
win32 api : http://undocumented.ntinternals.net/
A system-wide DLL, implementing the Windows native API. This is the lowest layer of code which is still in user mode. Its most important role is to make the transition to kernel mode for system call invocation. NTDLL also implements the Heap Manager, the Image Loader and some part of the user-mode thread pool. Although the native API is mostly undocumented.
win32 api : http://undocumented.ntinternals.net/
Subscribe to:
Comments (Atom)
Privileged arbitrary file read (CVE-2020-16938) with The Sleuth Kit
After I read one of post from twitter which is about @jonasLyk's CVE-2020-16938 , I've some idea to do without using 7 zip file ma...

-
I found one interesting post in medium which is here and i got some idea to bypass UAC . And I notice windows stor...
-
Version : AMD User Experience Program Launcher old version, (I forgot to snap). Operating System tested on : Windows 10 1909 (x64) Vulnera...
-
Version : AMD User Experience Program Launcher 1.0.0.1 (latest) Operating System tested on : Windows 10 1909 (x64) Vulnerability : RAMD U...