Operating System tested on: Windows 10 1909 (x64)
Vulnerability: AMD User Experience Program Launcher from Radeon Software Local Privilege Escalation through insecure file move
In these days,
I'm always look at the process monitor (procmon) and I found something which is interesting to me. That something which I found is the processes of AMD User Experience Program Launcher service.
Vulnerability Overview
AMD User Experience Program Launcher service which is auto start after PC reboot, it service run with AUEPLauncher.exe and that loaded AUEPMaster.exe . And it check 3 folders which are inside "C:\ProgramData\AMD\PPC" after about 30 seconds when service started.
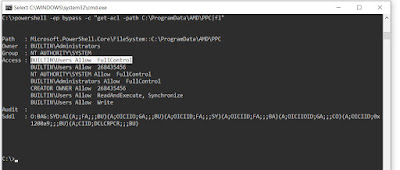
auto start service
and then "C:\ProgramData\AMD\PPC" can be accessed by buildin user with FullControl and also above 3 folders.
then, I created test file in temp folder "C:\ProgramData\AMD\PPC\temp" and restart the service and I check the procmon again. And I noticed some interested processes.
When I created file in temp folder "C:\ProgramData\AMD\PPC\temp\hellothere.txt", that created file change (as gz) in "C:\ProgramData\AMD\PPC\temp\hellothere.txt.gz" and then
moved (SetRenameInformationFile) into *send* folder "C:\ProgramData\AMD\PPC\send\hellothere.txt.gz" with SYSTEM privilege which can be Full controlled by BUILDIN\Users .
Why is this interesting? This presents the opportunity to use Symbolic Links during the move file operation to accomplish a privileged file write. How you might ask? The workflow would be like so:
Create the file in temp folder "C:\ProgramData\AMD\PPC\send\eop_filewrited.pwn" and it will move to send folder as gz file "C:\ProgramData\AMD\PPC\send\eop_filewrited.pwn.gz".
So, create a Symbolic Link on "C:\ProgramData\AMD\PPC\send\eop_filewrited.pwn.gz" that points to "C:\Windows\System32\evil_filewrited.txt" It should be noted that "C:\Windows\System32\evil_filewrited.txt" doesn't exist. And It's will write as C:\Windows\System32\evil_filewrited.txt with SYSTEM privilege which can be FullControl accessed by users.
Symbolic link:
recommend to read about symlink: James Forshaw's A Link to the past .
I used symboliclink-testing-tools which have been created by James Forshaw (@tiraniddo) from Project Zero.
Poc:
echo test123 > C:\ProgramData\AMD\PPC\temp\eop_filewrited.pwn
del /q C:\ProgramData\AMD\PPC\send\*
rmdir /q C:\ProgramData\AMD\PPC\send
CreateSymlink.exe C:\ProgramData\AMD\PPC\send\eop_filewrited.pwn.gz C:\windows\system32\evil_filewrited.txt
and restart the service (or reboot).
wait about 30 seconds after service restarted.
Get FullControl access on "C:\windows\system32\evil_filewrited.txt".
Then, I created the exploit poc script and I used @itm4n's UsoDllLoader as a privileged filewrite weapon to get system shell.
my poc script: https://github.com/sailay1996/amd_eop_poc
B00M !!!
logic bugs are fun.
happy hunting.
you can look up here if you're interested in hunting logical bugs.
https://github.com/sailay1996/awesome_windows_logical_bugs










No comments:
Post a Comment